Cybersecurity
Eksempler fra vores fællesskab
83 resultater for 'cybersecurity'

Network Cables
Match op
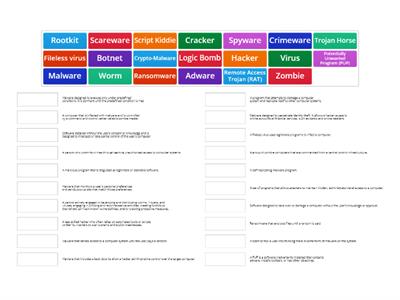
Security+: Malware Types
Match op
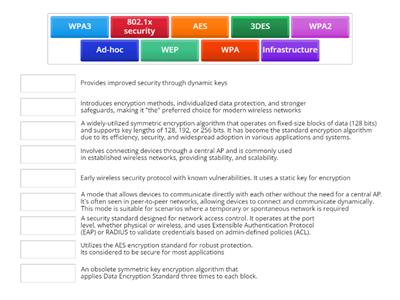
Wireless Security
Match op

Defense in Depth Principles
Match op
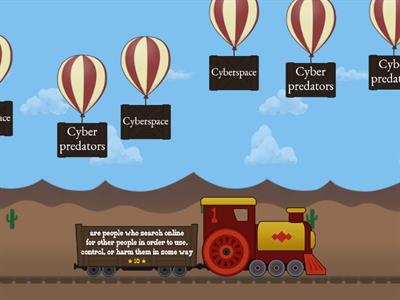
Cybersecurity
Ballon pop

Cybersecurity
Quiz

K-5 Cybersecurity Vocabulary
Find matchet

LESSON 4 - CYBERSECURITY
Anagram med ord
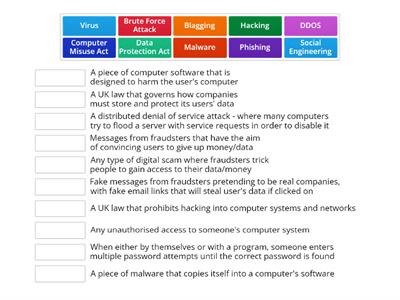
Cybersecurity Keyword Revision
Match op
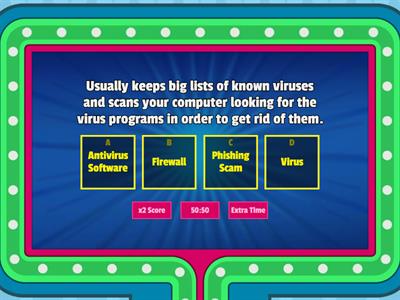
Cybersecurity and Crime
Gameshow quiz

Cybersecurity and CIA Triad
Match op

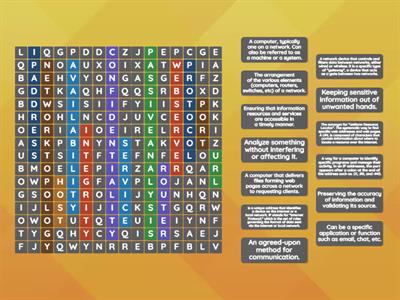
Advanced Cybersecurity Scanvenger Hunt
Find matchet
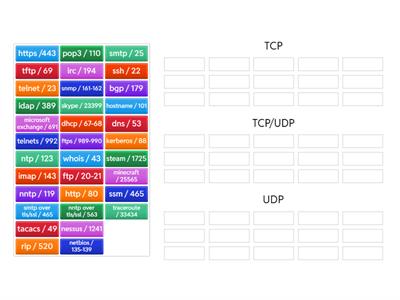
Ports and Protocols
Gruppesortering
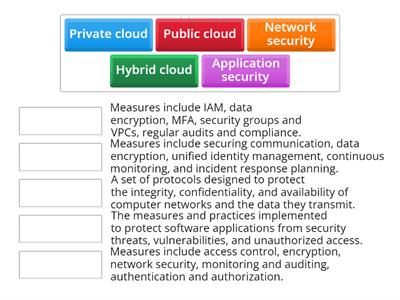
Cloud Security
Match op
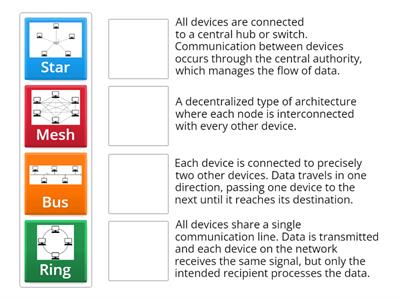
Network Topology
Match op
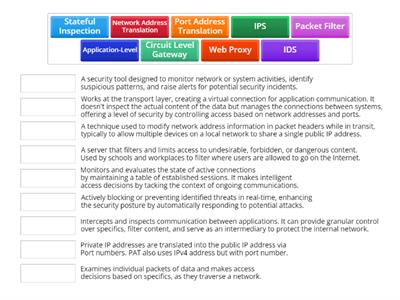
Network SecOps
Match op

Common Attacks and Threats
Match op
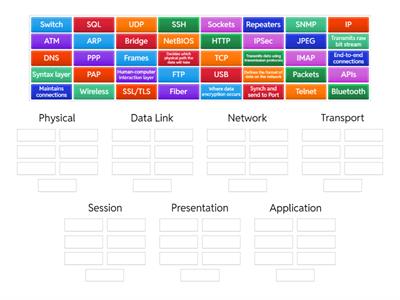
OSI Model
Gruppesortering

Virtualization and Cloud Computing
Match op
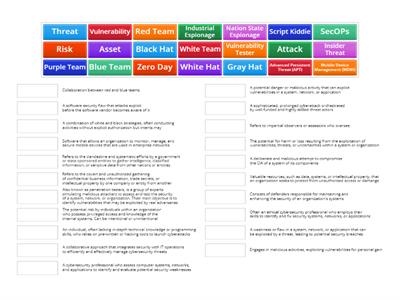
Network Security
Match op

Cyber Threats and Vulnerabilities
Flash-kort
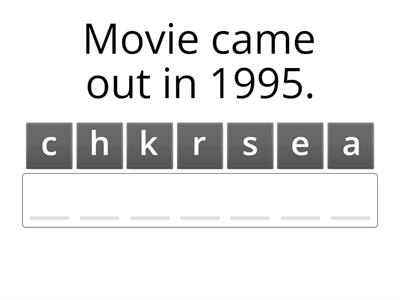
Cybersecurity
Anagram

Cybersecurity
Tilfældige kort

Cybersecurity
Gruppesortering
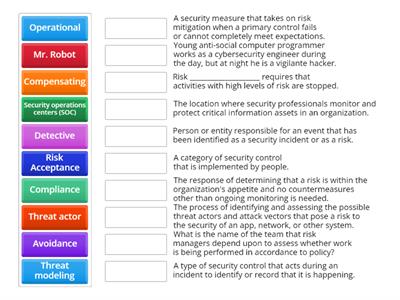
Cybersecurity Stuff
Match op

B2 Cybersecurity
Åbn boksen

Cybersecurity Vocabulary
Match op
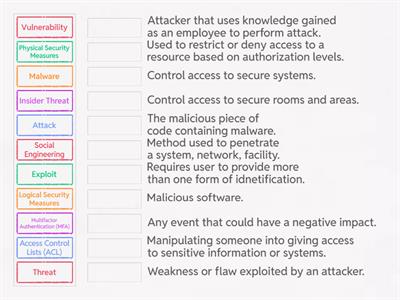
Cybersecurity Terminology
Match op

Cybersecurity All Ages
Udfyld sætningen

Evolution of Cybersecurity
Find matchet

Unit 1 Cybersecurity Vocabulary
Match op
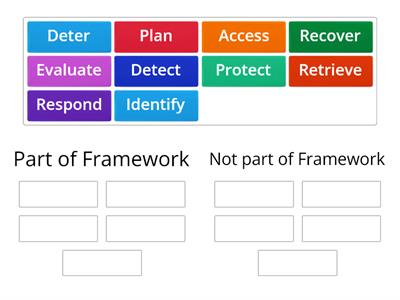
NIST Cybersecurity Framework
Gruppesortering
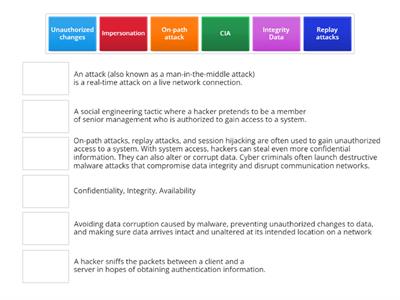
CyberSecurity - Integrity (CIA)
Match op
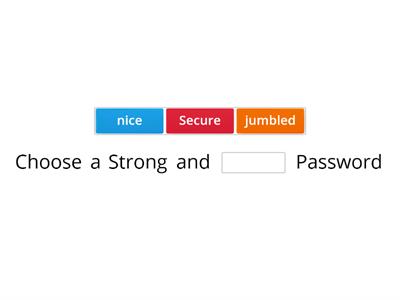
Lesson 04 - Cybersecurity/Cyberthreat
Udfyld sætningen
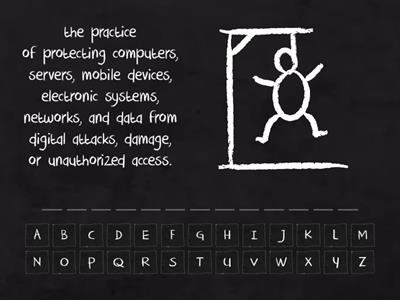
Cybersecurity Vocabulary Words
Hangman
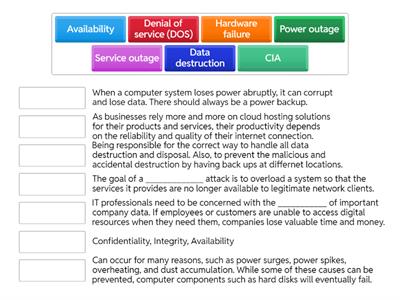
CyberSecurity - Availability (CIA)
Match op
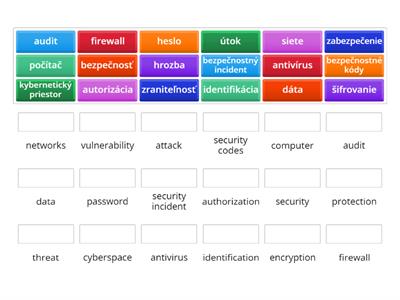
Cybersecurity nouns SK
Match op

Cybersecurity I - Game Show!!
Flyvemaskine
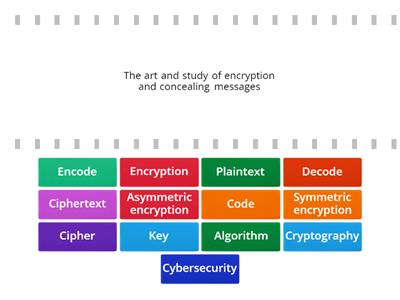
Advanced Cybersecurity Scavenger Hunt
Find matchet
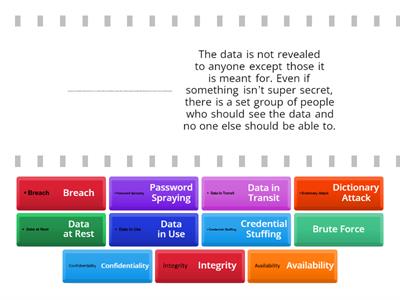
Cybersecurity Unit 0.1 - 1.1.3
Find matchet

03.08.24 Do Now U11L7 Cybersecurity
Labyrint jagt
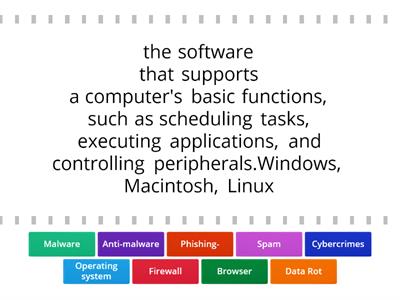
Lesson 4 Cybersecurity / Cyber Threats
Find matchet
04.04.24 Do Now U6L8 Cybersecurity
Vind eller tab quiz

CYBERSECURITY - PASSIVE ANALYSIS - ACTIVITY 2.1.2
Find matchet

04.03.24 Do Now U6L8 Cybersecurity
Match op
Cybersecurity Activity 3.1.2 Access Control
Ordsøgning

Overview of Cybersecurity & Digital Citizenship
Labyrint jagt