Information technology
Примеры из нашего сообщества
1 331 результатов для 'information technology'

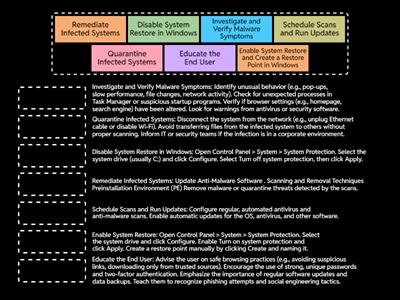
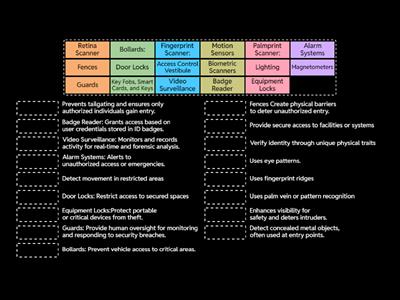
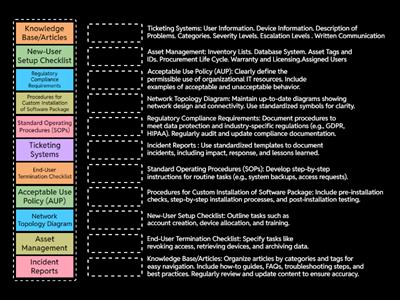
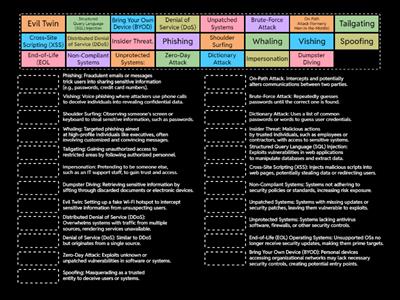
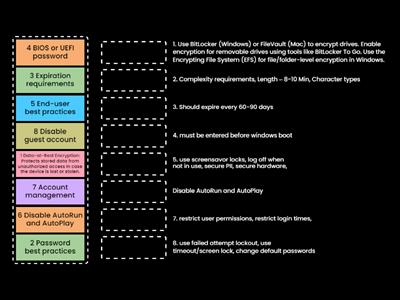
Malware - Comptia A+ 1102
Сопоставить

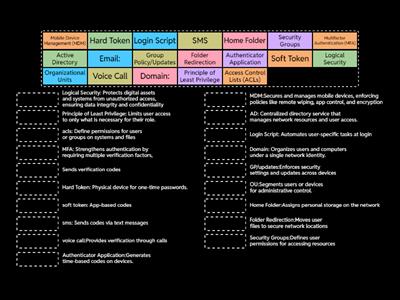
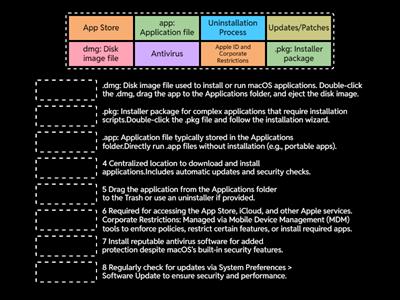
Microsoft Features and Tools - Comptia A+ 1102
Сопоставить

Social Engineering - Comptia A+ 1102
Сопоставить

Microsoft Features and Tools - CompTIA A+ 1102
Сопоставить

Windows Commands - Comptia A+ 1102
Сопоставить

steps for malware removal (Simple)
Сопоставить

IT Back up's
Сопоставить

a+ 1102 1.3 Microsoft Management Console
Сопоставить

a+ 1102 1.5 - Windows Settings
Сопоставить

a+ 1102 1.4 - The Windows Control Panel
Сопоставить

Common Port Numbers (Detailed)
Сопоставить

Text Annotations
Сопоставить

Text Features
Погоня в лабиринте

TECH SAVVY
Сопоставить

Tech Tools Word Search
Поиск слов

Microsoft Word Window Review
Диаграмма с метками

Microsoft Office Word
Погоня в лабиринте

t568-B | Ethernet UTP Wiring Standard
Сопоставить

CompTIA A+ 220-1101 Laser Printing Process
Диаграмма с метками

Technology
Сопоставить

Microsoft Office Excel
Самолет

Microsoft Excel Window Review
Диаграмма с метками

Personal Information Review
Викторина

PERSONAL INFORMATION
Случайное колесо

PERSONAL INFORMATION
Случайное колесо

Final review 2
Викторина

Technology
Анаграмма

Vocab 2 patent
Викторина

Label the Parts of an Online Article
Диаграмма с метками

review11 statistics
Сопоставить

Technology or Nature?
Самолет

EdTech Vocabulary Flashcards
Флэш-карты

T1_S5_ personal information
Викторина

Asking WH Questions to Get Information
Случайное колесо

Technology Wins The Game
Сопоставить

Personal Information
Сопоставить

Personal Information
Случайное колесо

US History Technology
Согласующиеся пары

Micro:Bit Activity 1
Диаграмма с метками

Social Networking & Gaming in the Classroom
Викторина "Игровое шоу"

Robots Pre-Quiz
Викторина "Игровое шоу"

Parts of an Email
Диаграмма с метками

Personal Information Questions
Случайные карты

Personal vs. Private Information
Погоня в лабиринте
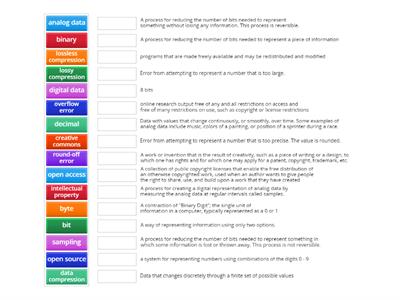
Unit 1 Digital Information
Сопоставить
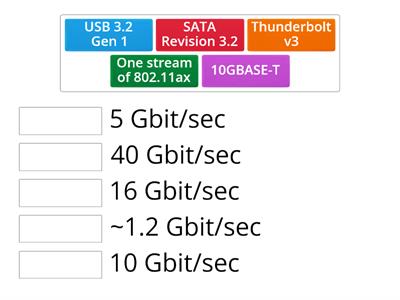
Comptia A+ 1101 Technology Throughput Practice
Сопоставить

Technology in Astronomy
Викторина "Игровое шоу"
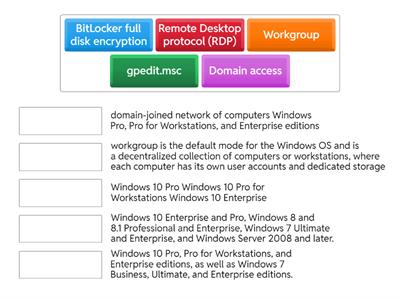
a+ 1102 1.1 os feature differences
Сопоставить

COLLOCATIONS IN INFORMATION TECHNOLOGY
Согласующиеся пары