Cybersecurity
Contoh dari komunitas kami
79 hasil untuk 'cybersecurity'

Network Cables
Permainan Pencocokan

Security+: Malware Types
Permainan Pencocokan

Pretexting, Preloading, and Impersonation CompTIA 601
Permainan Pencocokan

Defense in Depth Principles
Permainan Pencocokan

Defense in Depth Principles (Reversed)
Permainan Pencocokan

Defense in Depth (Definition Exercise)
Permainan Pencocokan

Cybersecurity
Pecah Balon

Cybersecurity
Kuis

K-5 Cybersecurity Vocabulary
Menemukan kecocokan

Cybersecurity Keyword Revision
Permainan Pencocokan

LESSON 4 - CYBERSECURITY
Benarkan Kalimat

Cybersecurity and Crime
Kuis gameshow

Cybersecurity and CIA Triad
Permainan Pencocokan

Advanced Cybersecurity Scanvenger Hunt
Menemukan kecocokan

Ports and Protocols
Pengurutan grup

Cloud Security
Permainan Pencocokan

Wireless Security
Permainan Pencocokan

Common Attacks and Threats
Permainan Pencocokan

Network SecOps
Permainan Pencocokan

Virtualization and Cloud Computing
Permainan Pencocokan

Network Security
Permainan Pencocokan

Network Topology
Permainan Pencocokan

Cyber Threats and Vulnerabilities
Kartu lampu kilat

OSI Model
Pengurutan grup

Cybersecurity
Anagram

Cybersecurity
Kartu acak

Cybersecurity Stuff
Permainan Pencocokan

Cybersecurity Vocabulary
Permainan Pencocokan

Cybersecurity Terminology
Permainan Pencocokan

B2 Cybersecurity
Membuka kotak

Unit 1 Cybersecurity Vocabulary
Permainan Pencocokan

NIST Cybersecurity Framework
Pengurutan grup

Evolution of Cybersecurity
Menemukan kecocokan

Cybersecurity All Ages
Lengkapi kalimatnya

CyberSecurity - Integrity (CIA)
Permainan Pencocokan

Lesson 04 - Cybersecurity/Cyberthreat
Lengkapi kalimatnya

Cybersecurity - Confidentiality (CIA)
Permainan Pencocokan

Cybersecurity Vocabulary Words
Si Algojo

CyberSecurity - Availability (CIA)
Permainan Pencocokan

Cybersecurity nouns SK
Permainan Pencocokan

Advanced Cybersecurity Scavenger Hunt
Menemukan kecocokan

Cybersecurity I - Game Show!!
Pesawat Terbang

Cybersecurity Unit 0.1 - 1.1.3
Menemukan kecocokan

Cybersecurity Activity 3.1.2 Access Control
Mencari Kata

04.03.24 Do Now U6L8 Cybersecurity
Permainan Pencocokan

CYBERSECURITY - PASSIVE ANALYSIS - ACTIVITY 2.1.2
Mencari Kata

CYBERSECURITY - PASSIVE ANALYSIS - ACTIVITY 2.1.2
Menemukan kecocokan

Lesson 4 Cybersecurity / Cyber Threats
Menemukan kecocokan

03.08.24 Do Now U11L7 Cybersecurity
Pengejaran dalam labirin
04.04.24 Do Now U6L8 Cybersecurity
Kuis Menang atau kalah

Lesson 4 Cybersecurity / Cyber Threats
Permainan Pencocokan

Cybersecurity: Lesson 3.1.3 - Analyzing Processes
Pengejaran dalam labirin
Lesson 4 Cybersecurity / Cyber Threats
Teka Teki Silang

Overview of Cybersecurity & Digital Citizenship
Pengejaran dalam labirin
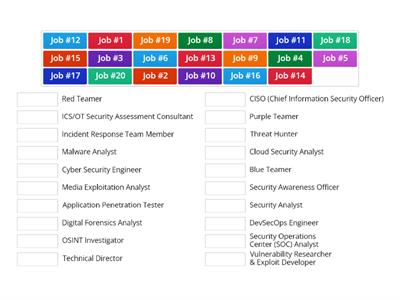
20 Coolest Careers in CyberSecurity
Permainan Pencocokan
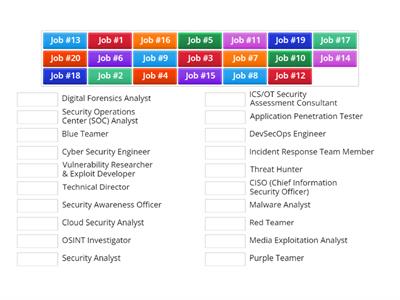
20 Coolest Careers in CyberSecurity!
Permainan Pencocokan

